Portco Cyber Defense
Increase security posture transparency and reporting for portfolio companies.
Portco Process
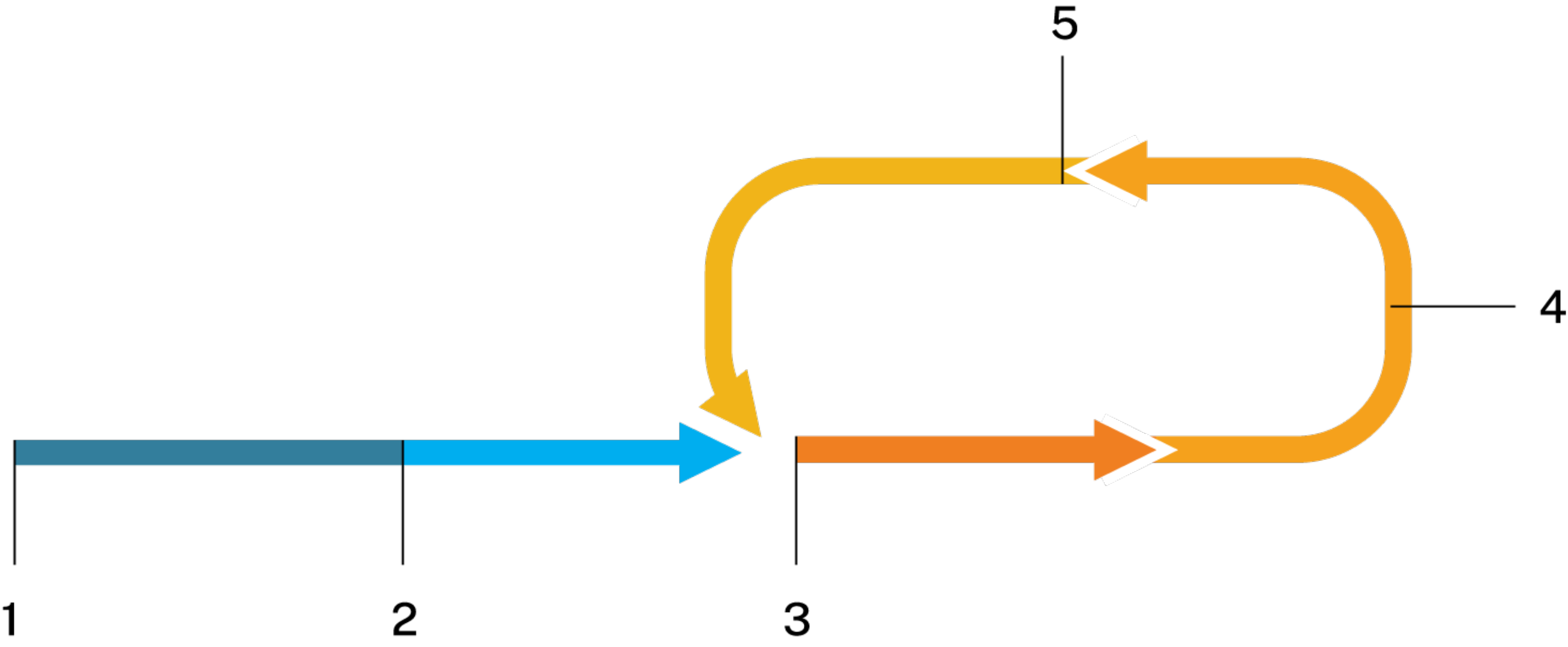



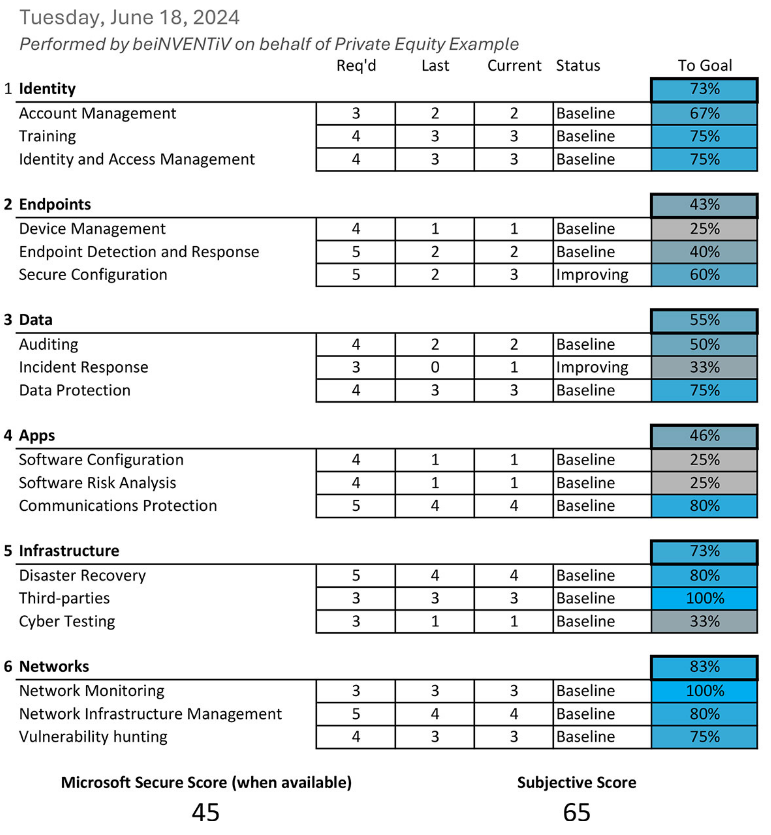
Before we begin, we meet with the PE firm to understand the goals for each portco and establish target values for 20 key security indicators. Our key indicators are based on a common Zero-Trust Framework, yet each portco will have a unique sliding scale that takes into account business objectives, mitigating factors, and compensating controls. No two portcos are identical and their ideal cybersecurity posture will balance optimal practices with practical constraints, acceptable risks, and budgets.
We then collect data from the portco IT teams through stakeholder interviews and measure the current environment against that benchmark to determine the initial state of the organization. This analysis provides each portco’s IT team with the knowledge needed to make informed decisions about where and how to implement changes to mitigate risks effectively.




We then collect data from the portco IT teams through stakeholder interviews and measure the current environment against that benchmark to determine the initial state of the organization. This analysis provides each portco’s IT team with the knowledge needed to make informed decisions about where and how to implement changes to mitigate risks effectively.



Periodic verification of planned and unplanned security initiatives and shifts in cybersecurity threats is required to ensure continued portco protection.
Each quarter, we work with the portcos to reassess the organization on the same indicators, taking into account any changes that are made – whether positive or negative – and provide an updated scorecard that can track the organization’s progress toward better cybersecurity. The portco’s IT can then use this scorecard to confirm progress and make informed decisions about where to focus their resources in the coming quarter to make impactful changes.